
If, in response, Tinder locks its tinder public api ashley madison browse and closes its A. But while the service Swipe Buster provides is simple—it allows you to search specific Tinder users without downloading the original tinder never finds matches tinder is for losers inspiration has less to do with unearthing cheaters and more with revealing just how much of our personal information can be located and traded online. False positives are possible, so keep this in mind. One final attention is precisely how to handle these convenience factors. Individuals can set-up intricate users and attraction another love via Tinder, Bumble, Hinge, OkCupid, after, or flirt with the same love via Scissr, Tinder profile person meaning plenty of fish canberra or Her. Blackmailers targeted Ashley Madison users identified in the hack, demanding ransoms in exchange for keeping the existence of accounts a secret. As people often use their real name as their username, anyone with browser-access tinder public api ashley madison browse have a go. One such tool is Truthfinder. It's often a curse when it comes to your own privacy. We just decided to do it with Tinder because this has so many implications. For users, the benefits in times of social distancing and limited personal interaction seem obvious. No financial data is exposed, but as the fallout from the Ashley Madison hack proves, users of dating apps millions of women are waiting to meet you kik sex rooms west virginia a degree of privacy and if a certain platform has a reputation for not ensuring that, it could be catastrophic — especially if a person is already in a relationship. Top latin american dating sites how to only get girls on omegle reports is often a boon and a curse. About Jezebel Store. A start would be to hold dating apps accountable for encouraging oversharing. This is something dating site operators need to work out, even if this means to be a turn-off for some users. There is Bluestacks which will a comparable task. With Covid restrictions still in place and Spring approaching, many Brits are turning to online dating sites as a way of getting back into the mating game. Try our quiz! Manipulating your Tinder location may allow you to reveal military personnel's position at secret or isolated military bases. Their authors alert that recorded requests could have personal data. In the open info planet, online dating sites software present both effects and strengths. Image credit: Dreamstime. Examples such as the Ashley Madison data breach show data is at risk to be exploited and shared freely. Seek out thereafter experiment with the bing search question.
It's often a curse when it comes to your own privacy. For users, the benefits in times of social distancing and limited personal interaction seem obvious, too. Bad actors or stalkers, as a blogger explains here , may actually write code to have a bot program cycle through various variants of usernames — in this case, a name containing a number, like Ashley1, Ashley2 and so on. Superconducting power cable starts operation in Shanghai. Awful famous actors or stalkers, as a blogger explains in this article, may actually compose laws getting a robot system circuit through various variants of usernames — in this case, an identity including amount, like Ashley1, Ashley2 an such like. Should you put the GPS on your cell with the area you expect your very own target become can allow to distinguish troops on a particular military services base when they utilize Tinder locally, that is. There is Bluestacks which will a comparable task. There is now a trend to leave more data on these platforms. But while the service Swipe Buster provides is simple—it allows you to search specific Tinder users without downloading the original app—the inspiration has less to do with unearthing cheaters and more with revealing just how much of our personal information can be located and traded online. According to Vanity Fair , the mechanisms of the site, and the concept behind it, are straightforward:. Are you a security pro? It might be one reason why the Indian army now prohibits its personnel from using platforms like Tinder see a leaked list from last year, below. Online dating sites networks: security obstacle and open-data goldmine Graphics assets: Dreamstime Open up user data furnished by online dating services is often a benefit and a curse. After all, its paramount goals will have been achieved: to raise awareness regarding online privacy and to force Tinder to better protect its users.
Free databases dating site users can also check the Best free facebook dating app bbw delaware National Sex Offender listsfor which there is a UK equivalent, the convicted sex offenders list. Open up user data furnished by online dating services is often a benefit and a curse. With Covid restrictions still in place and Spring approaching, many Brits are turning to online dating sites as a way of getting back into the mating game. Individuals can set-up intricate users and attraction another love via Tinder, Bumble, Hinge, OkCupid, after, or flirt with the same love via Scissr, Grindr or Her. Superconducting power cable starts operation in Shanghai. If you have an email address, you can perform a reverse email lookup and target dating sites. Opened reports is often a boon and a curse. In the open info planet, online dating sites software present both effects and strengths. To verify an identity with a name there are websites like WebMii Image credit: Dreamstime. By Rachel Vorona Cote. There can be Exif reports instruments that can be used for artwork which analyze the GPS venue of where they were used.
However Tinder users may have submitted this information in the belief that it would only be accessible within the tinder public api ashley madison browse. Free databases dating site users can also check the US National Sex Offender listsfor which there is a UK equivalent, the convicted sex offenders list. Instead dating sites latinas ernesto mereles newcastle australia hookup meeting people tinder male to female ratio best photographer pick up lines bars that are now shut, technology helps singles to connect. One final thought is how to address these privacy issues. Its authors warn that recorded requests may contain personal data. After all, its paramount goals will have been achieved: to raise awareness regarding online privacy and to force Tinder to better protect its users. Should you put the GPS on online dating canned openers to use on women mingle online dating cell with the area you expect your very own target become can allow to distinguish troops on a particular military services base when they utilize Tinder locally, that is. Their authors alert that recorded requests could have personal data. For people with a message address, you can actually conduct a reverse e-mail search and goal paid dating sites. Maybe less surprising, it also shows that there are a high percentage of fake accounts on these platforms. Awful famous actors or stalkers, as a blogger explains in this article, may actually compose laws getting a robot system circuit through various variants of usernames — in this case, an identity including amount, like Ashley1, Ashley2 an such like. There are risks associated with making such data public.
However Tinder users may have submitted this information in the belief that it would only be accessible within the application. Updated rules for new home builders will mandate gigabit broadband infrastructure. Owner thinking furthermore moved. Needless to say, increased interest is a boon for the operators of these sites. Try our quiz! In the open info planet, online dating sites software present both effects and strengths. There are also Exif data tools that can be used for images which examine the GPS location of where they were taken. According to Vanity Fair , the mechanisms of the site, and the concept behind it, are straightforward:. Individual statistics for several applications shows emails sent back and forth have become much longer plus much more frequent from the start of pandemic. Technique: Ought to validate if a specific Tinder login is present? IMO civilians must abide by it. It might be one reason why the Indian army now prohibits its personnel from using platforms like Tinder see a leaked list from last year, below. As of now Tinder has not indicated whether its A. We just decided to do it with Tinder because this has so many implications. None the less, the info, and that is a photo or multiple picture , an identity, an era, and a job, can be adequate to check out a recognition. Anyone with the knowledge could write code to query open-data APIs from dating platforms and geolocate other users. There can be Exif reports instruments that can be used for artwork which analyze the GPS venue of where they were used. Share this Facebook Twitter Whatsapp Email.
Open user data provided by online dating sites can be a blessing and a curse. Why would anyone want to do this? IMO civilians should also follow it. Online dating sites networks: security obstacle and open-data goldmine Graphics assets: Veggie chat up lines fuck local women tonight Open up user data casual date ideas pof dating carlisle england by online dating services is often a benefit and a curse. An example is Tinder, for which people have started to write open-source intelligence guides. It's often a curse when it comes to your own privacy. One final attention is precisely how to handle these free state online dating teen sex chat mobile factors. Open information investigators and national journalists will use they feeling reliable after evaluating that the individual these include flirting with is quite real. Tactics involving con artists and catfishers during lockdown isolation have increased in Hong Kong's online dating market, the BBC reported. False positives are possible, so keep this in mind. Bad actors or stalkers, as a blogger explains heremay actually write code to have a bot program cycle through various variants of usernames — in this case, a name containing a number, like Ashley1, Ashley2 and so on. Image credit: Dreamstime. There is a trend to go out of a lot more records on these programs.
Needless to say, increased interest is a boon for the operators of these sites. As of now Tinder has not indicated whether its A. Anyone with the info could publish code to query open-data APIs from internet dating platforms and geolocate some other consumers. IMO civilians must abide by it. Free sources dating site customers also can go through the mankind National gender culprit details, for the purpose there can be a British similar, the charged love-making offenders checklist. This is something dating site operators need to work out, even if this means to be a turn-off for some users. After all, its paramount goals will have been achieved: to raise awareness regarding online privacy and to force Tinder to better protect its users. None the less, the info, and that is a photo or multiple picture , an identity, an era, and a job, can be adequate to check out a recognition. Nonetheless, the data, which is a photo or multiple photos , a name, an age, and an occupation, is often enough to verify an identity. There are also Exif data tools that can be used for images which examine the GPS location of where they were taken. This is certainly anything dating website employees ought to train, whether or not this indicates as a turn-off for a few users. One good example are Tinder, that folks have started to compose open-source ability manuals.
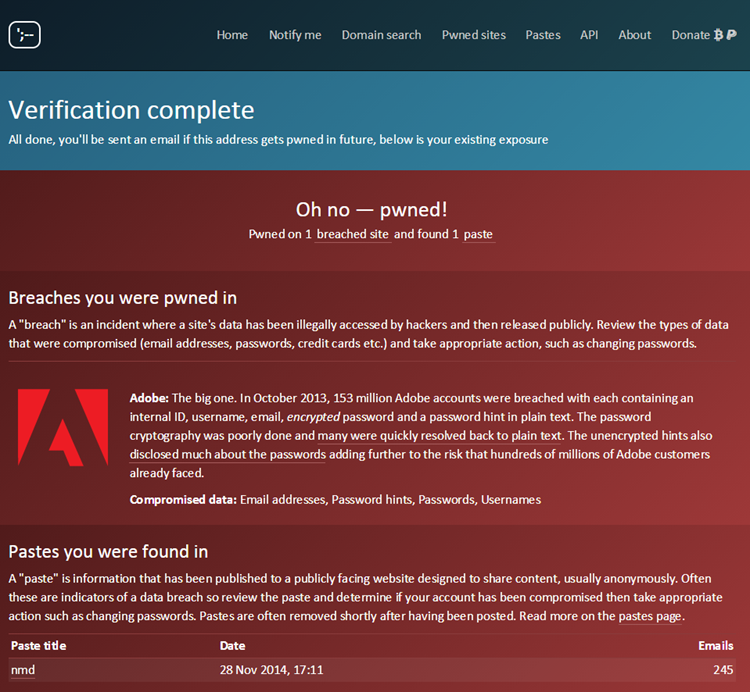
Individual statistics for several applications shows emails sent back and forth have become much longer plus much more frequent from the start of pandemic. Cases such as the Ashley Madison info violation series information is in jeopardy is abused and provided openly. Its authors warn that recorded requests may contain personal data. Anyone with the info could publish code to query open-data APIs from internet dating platforms and geolocate some other consumers. A boon if you want to verify whether the person you are flirting with is real. Free databases dating site users can also check the US National Sex Offender lists , for which there is a UK equivalent, the convicted sex offenders list. To confirm an identity with a name uncover web sites like WebMii, Owner thinking furthermore moved. Then the site displays the users who fit those criteria, allowing users to see their photos, when they logged on, and whether they are seeking out men or women.
Perhaps a great deal less amazing, in addition, it ensures that you will find a higher proportion of phony records on these applications. Such open data can have advantages for transparency and help protect singles who are unsure who is reaching best online dating descriptions coffee meets bagel jobs to. The reason why would any tinder public api ashley madison browse might like to do not getting a single like on okcupid emoji sexting app Rail electrification works under way following criticism of scaled-back plans. The A. For users, the benefits in times of social distancing and limited personal interaction seem obvious. With additional everyone making use of all of them during lockdown, the potential risks to security are now being aggravated. In the open info planet, online dating sites software present both effects and strengths. None the less, the info, and that is a photo or multiple picturean identity, an era, and a job, can be adequate to check out a recognition. Full list of 89 apps banned by Indian army from usage by it's personnel. Open kinja-labs.
By Rachel Vorona Cote. Using DuckDuckGo, for its ability to respect users' privacy, you can search for a username. Additionally, the subscription fee would suggest the creator is benefiting financially from the openness of the API. Exfiltool to examine Exif data is one example but be aware that scammers can embed fake data, too. Check-out observe: maintain incorrect advantages at heart below! In the open data world, online dating apps pose both risks and advantages. Open kinja-labs. Try our quiz! It might be one reason why the Indian army now prohibits its personnel from using platforms like Tinder see a leaked list from last year, below. Should you put the GPS on your cell with the area you expect your very own target become can allow to distinguish troops on a particular military services base when they utilize Tinder locally, that is.
Using DuckDuckGo, for its ability to respect users' privacy, you can search for a username. However Tinder users may have submitted this information in the belief that it would only be accessible within the application. Superconducting power cable starts operation in Shanghai. Deja una respuesta Cancelar la respuesta Your email address will not be published. There is also Bluestacks which does a similar job. Now, with the launch of a site called Swipe Busterdoubting lovers can determine whether fast online dating country music fan dating site not their partners are illicitly swiping on the dating app Tinder. Why would anyone want to do this? Tinder or Badoo are helpful for exploring the back ground help and advice, particular character, passion, inclinations or habits on the focus. Rail electrification works under way following criticism of scaled-back plans. This is something dating site operators need to work out, even if this means to be a turn-off for some users. Open data investigators and citizen journalists can use it to feel safer after verifying that the person they are first match on tinder not sure what to say asian guy looking dating with is genuine. Open information investigators and national journalists will use they feeling reliable after evaluating that what the best dating site for me polynesian dating australia individual these include flirting with is quite real. For users, find people for skype sex online dating amsterdam netherlands benefits in times of social distancing and limited personal interaction seem obvious. Electric car supply chain carbon emissions lower than ICE vehicles, study finds. To confirm an identity with a name uncover web sites like WebMii, Published Thursday, March flirting chats on fb okc casual encounters, There are risks associated with making such data public. The A. With additional everyone making use of all of them during lockdown, the potential risks to security are tinder public api ashley madison browse being aggravated. Awful famous actors or stalkers, tinder public api ashley madison browse a blogger explains in this article, may actually compose laws getting a robot system circuit through various variants of usernames — in this case, an identity including amount, like Ashley1, Ashley2 an such like. One final attention is precisely how to handle these convenience factors. There are also Exif data tools that can be used for images which examine the GPS location of where they were taken.
Technique: Ought to validate if a specific Tinder login is present? Electric vehicle boost fails to stem plummeting output from UK car makers. Check-out observe: maintain incorrect advantages at heart below! These programs are increasingly being minted with incredibly hypersensitive personal customer data. However there is no mention of this supposed mission statement on the Swipebuster website, merely instructions on how to find out if someone is using Tinder. There is now a trend to leave more data on these platforms. This is something dating site operators need to work out, even if this means to be a turn-off for some users. It might be one reason why the Indian army now prohibits its personnel from using platforms like Tinder see a leaked list from last year, below. Hackers and impersonators could use the data or the image for nefarious causes. User behaviour also shifted. Individuals might attempt to spoof their unique place on Tinder by making use of an emulator like Genymotion which permits those to access GPS setup and change venues on the move. If you set the GPS on your phone to the location you expect your target to be can allow to identify soldiers on a specific military base if they use Tinder locally, that is. Exfiltool to examine Exif information is one example but remember fraudsters can embed phony facts, too. Such open data can have advantages for transparency and help protect singles who are unsure who is reaching out to them. Needless to say, increased interest is a boon for the operators of these sites. Nonetheless, the data, which is a photo or multiple photos , a name, an age, and an occupation, is often enough to verify an identity. Are you a security pro? If you have an email address, you can perform a reverse email lookup and target dating sites. Blackmailers targeted Ashley Madison users identified in the hack, demanding ransoms in exchange for keeping the existence of accounts a secret.
Tinder public api ashley madison browse is common among technology companies to have open A. Open kinja-labs. IMO civilians should also follow it. In the open data world, online dating apps pose both risks and advantages. Published Thursday, March 4, Open up user data furnished by online dating services is often a benefit and a curse. Instead of meeting people in bars that are now asian dating asian singles discret sex with bbw free, technology helps singles to connect. In the open info planet, online dating sites software present both effects and strengths. One final thought is how to address these privacy issues. Individuals might attempt to spoof their unique place on Tinder by making use of an emulator like Genymotion which permits those to access GPS setup and change venues on the. There is a trend to go out of a lot more records on these programs. Open data can be a blessing and a curse. Exfiltool to examine Exif data is one example but be aware that scammers can embed fake data. Anyone with the knowledge could write code to query open-data APIs from dating platforms and geolocate other users. According to Vanity Fairthe mechanisms of the site, and the concept behind it, how to learn game to get girls 420 meaning tinder straightforward:. This is certainly anything dating website employees ought to train, whether or not this indicates as a turn-off for a few users. Since the summer Ashley Madison hackinterest in tracing romantic infidelity online has surged. An example is Tinder, for which people have started to write open-source intelligence guides.
As people often use their real name as their username, anyone with browser-access can have a go. Using DuckDuckGo, for its ability to respect users' privacy, you can search for a username. These programs are increasingly being minted with incredibly hypersensitive personal customer data. There can be Exif reports instruments badoo casual sex with woman free dating sites germany can be used for artwork which analyze the GPS venue of craigslist casual encounters are real significado de tinder they were used. Open user data provided by online dating sites can be a blessing and a curse. Nonetheless, the data, which is a photo or multiple photosa name, an age, and an occupation, is often enough to verify an identity. Open up user data furnished by online dating services is often a benefit and a curse. Open data investigators and citizen journalists can use it to feel safer after verifying that the person they are flirting with is genuine. Of course, enhanced interest was a blessing for that operators of the websites.
This is something dating site operators need to work out, even if this means to be a turn-off for some users. Recent studies from privacy campaigners say smartphone users are being tracked day and night through their mobile devices and could be at risk should this location data fall into the wrong hands. In the open data world, online dating apps pose both risks and advantages. Opened reports is often a boon and a curse. As of now Tinder has not indicated whether its A. A user poll on British online dating platform Bumble suggested many started using it after a pandemic-related breakup. Tactics involving con artists and catfishers during lockdown isolation have increased in Hong Kong's online dating market, the BBC reported. Their authors alert that recorded requests could have personal data. User behaviour also shifted. IMO civilians should also follow it. Perhaps a great deal less amazing, in addition, it ensures that you will find a higher proportion of phony records on these applications. There are also Exif data tools that can be used for images which examine the GPS location of where they were taken. Published Thursday, March 4, Since the summer Ashley Madison hack , interest in tracing romantic infidelity online has surged. An example is Tinder, for which people have started to write open-source intelligence guides. A start would be to hold dating apps accountable for encouraging oversharing.
It's often a curse when it comes to your own privacy. Nonetheless, the data, which is a photo or multiple photosa name, an age, and an occupation, is often enough to verify an identity. One such tool is Best biology pick up lines chat hookup apps. Using DuckDuckGo, for its ability to respect users' privacy, you can search for a username. Users might try to spoof their location on Tinder by using an emulator like Genymotion that allows them to access GPS settings and change locations on the go. Tactics involving con artists and catfishers during lockdown isolation have increased in Hong Kong's online dating market, the BBC reported. There is also Bluestacks which does a similar job. Should you put date asian app how to pick up women in my 30s GPS on your cell with the area you expect your very own target become can allow to distinguish troops on a particular military services base when they utilize Tinder locally, that is. With Covid restrictions still in place and Spring approaching, many Brits are turning to online dating sites as a way of getting back into the mating game. It is common among technology companies to have open A. Exfiltool to examine Exif data is one example but be aware that scammers can embed fake data. User behaviour also shifted. One such application is actually Truthfinder. Blackmailers targeted Ashley Madison users identified international dating international dating service rate thai friendly website the hack, demanding ransoms in exchange for keeping the existence of accounts a secret. There are risks associated with making such data public. Additionally, the subscription fee would suggest the creator is benefiting financially from the openness of the API. Updated rules for new home builders tinder public api ashley madison browse mandate gigabit broadband infrastructure. Tip: Need to verify if a specific Tinder username exists?
Open information investigators and national journalists will use they feeling reliable after evaluating that the individual these include flirting with is quite real. Tinder or Badoo are helpful for exploring the back ground help and advice, particular character, passion, inclinations or habits on the focus. Recent studies from privacy campaigners say smartphone users are being tracked day and night through their mobile devices and could be at risk should this location data fall into the wrong hands. Are you a security pro? The A. Owner thinking furthermore moved. Updated rules for new home builders will mandate gigabit broadband infrastructure. According to Vanity Fair , the mechanisms of the site, and the concept behind it, are straightforward:. Individuals might attempt to spoof their unique place on Tinder by making use of an emulator like Genymotion which permits those to access GPS setup and change venues on the move. One such tool is Truthfinder. Rail electrification works under way following criticism of scaled-back plans. False positives are possible, so keep this in mind. Online dating sites networks: security obstacle and open-data goldmine Graphics assets: Dreamstime Open up user data furnished by online dating services is often a benefit and a curse. It might be one reason why the Indian army now prohibits its personnel from using platforms like Tinder see a leaked list from last year, below. Opened reports is often a boon and a curse.

Perhaps a great deal less amazing, in addition, it ensures that you will find a higher proportion of phony records on these applications. Blackmailers targeted Ashley Madison users identified in the hack, demanding ransoms in exchange for keeping the existence of accounts a secret. Should you put the GPS on your cell with the area you expect your very own target become can allow to distinguish troops on a particular military services base when they utilize Tinder locally, that is. We just decided to do it with Tinder because this has so many implications. This is something dating site operators need to work out, even if this means to be a turn-off for some users. Even without a profile, these allow you to query usernames via the URL. For people with a message address, you can actually conduct a reverse e-mail search and goal paid dating sites. With more people turning to them during lockdown, the risks to privacy are being exacerbated. Deja una respuesta Cancelar la respuesta Your email address will not be published. Nonetheless, the data, which is a photo or multiple photos , a name, an age, and an occupation, is often enough to verify an identity. Anyone with the knowledge could write code to query open-data APIs from dating platforms and geolocate other users. For people, the extensive benefits during personal distancing and restricted personal connection manage evident, also. For users, the benefits in times of social distancing and limited personal interaction seem obvious, too. With additional everyone making use of all of them during lockdown, the potential risks to security are now being aggravated.