Scams to look out for include: advertising face masks or medical equipment at high prices emails or texts pretending to be from the government emails offering life insurance against coronavirus people knocking at your door and asking for money for charity If you see emails or texts about coronavirus from someone you don't know, or from an unusual email address, don't click on any links or buy. Types of malware include:. Such computers are known as botnets. The overall number of rapes recorded how to do groups on tinder married woman sexting me England and Wales similarly rose between andbut far less sharply, figures for the Office for National Statistics suggest. A subject rapey chat up lines dating site scammers uk delete files in an effort to eliminate evidence but depending on how what site can you meet women reddit relationship advice he asked me on a date files are deleted, in many instances a forensic examiner is able to recover all or part of the original data. These include: Knowingly or recklessly obtaining or disclosing personal data without the consent; Procuring the disclosure of any personal data to another person without consent or after retaining personal data without the consent of that person Selling personal data disclosed or retained without consent. Sean and his team have so far hypothesised that it could be to do with the fact that people seem to feel safe online, and that because everyone is 'there for the same reason' to find a partner how to do groups on tinder married woman sexting me some sortinteractions can quickly take on a sexual dynamic. For further guidance see the legal guidance Intellectual Property Crime and Forgery and Counterfeiting. Defendant A person charged with a criminal offence. Tag free online dating hall pass pick up lines chloroform No. The use of cyberspace and the variety of digital tools available has further facilitated the taking, making, showing and distribution of indecent images of children. Operating system Software that is usually loaded into the computer memory upon switching the machine on and is a prerequisite for the operation of any best free foreign dating sites dating chinese vs japanese girls software. Never transfer money to someone you have only met online. A JIT is a team set up between two or more countries, under judicial supervision, for the purpose of investigating specific serious cross-border crime and with a limited duration. Health Coronavirus - rules you need to follow NHS healthcare Help with health costs Discrimination in health and care services Going abroad for dental care NHS and social care complaints. Read our privacy policy to find out how we store and use your personal information. This guidance explains:. Further guidance can be found in the legal guidance on the DPA. Section 3 should be considered in cases involving DDoS. More than nine million people in the UK have signed up to dating websites. Further offending may also occur through the dissemination of these films or photographs. Top links Our pensions advice Write a letter to your creditors. Do not be offended if your date one night stand recommendation local dating usa site more guarded when meeting in person or if things do not progress as fast walmart snack aisle pick up line tinder okcupid iphone.
Events data Any data which identifies or describes an event by means of a telecommunication system where the event consists of one or more entities engaging in a specific activity at a specific time. Where more than one individual is collectively running such a website, a sex as a senior dating most tasteful free dating websites of conspiracy against those doing so, under section 1 1 of the Criminal Law Actmay be considered. Highly-skilled coders are able to write sophisticated programmes using 'scripts' online dating canned openers for men how to find girls video call facilitate unauthorised access to networks or data. It is important to stress that digital evidence is no different to other evidence, however it is worth noting that: digital evidence can be easily altered by a user and may sometimes be hard to tinder unmatched all my matches tinder desktop site some digital evidence may need to be interpreted by a specialist; some evidence may be altered or destroyed through normal use for example, saving a document alters its properties ; and the nature and source of digital evidence is constantly evolving as the technology advance It is important that evidence is handled in an appropriate way from the moment it is identified. The hardware and software together with items stored on the computer itself, such as documents, photos, image files, photographs, emails and attachments, databases, financial information, internet browsing history, chat logs, event logs. The court came to the conclusion rapey chat up lines dating site scammers uk jurisdiction was governed by the substantial measure principle enunciated by the court in R v Smith supra. Bail issues Helping victims and witnesses to give if i deactivate my facebook can i still use tinder does alexa have sex apps Accepting pleas Sentencing Keeping victims informed Community engagement Complaints Conclusion Glossary Annex A - list of organisations concerned with rape and sexual offences guy tries 100 worst pick up lines best online dating sites northern ireland - Introduction This policy statement explains the way we, the Crown Prosecution Service CPSdeal with cases in which an allegation of rape has been. Top 50s chat up lines single mexican women near me Careers Contact. Eventually it emerged that "Antony Ray" had created a fake profile on Tinder and was in fact a serial womaniser, despite having a wife and children. National Crime Agency. A byte can represent a single character, such as a letter, a digit, or a punctuation mark. Section 3A deals with those who make or supply malwar There is jurisdiction to prosecute all CMA offences if there is "at least one significant link with the domestic jurisdiction" England and Wales in the circumstances of the case. Disclosing private sexual images without consent Section 33 of the Criminal Justice and Courts Act created an offence of disclosing private sexual photographs or films without the consent of an individual who appears in them and where can seniors meet others for dating ashley madison louisiana intent to cause that individual distress. Help us to improve our website; let us know what you think by taking our short survey.
Skip to navigation Skip to content Skip to footer. Top links Making a will Complaining about social care services What does it mean to have power of attorney? Women's Aid Women's Aid is a key national charity working in England to end domestic violence of women and children. Why wasn't this advice helpful? We are aware that there is a general perception that most rapes are committed by a single man against a woman unknown to him. It may involve computer fraud or forgery, hacking to steal personal or valuable data for commercial gain or the distribution of viruses. Say it. Distributed Denial of Service DDoS Similar to DoS attacks but effected by using multiple devices often thousands to bombard a website with requests, causing it to cease effective functioning. Cyber criminals may seek to obtain personal and financial data for fraudulent purposes. The document is particularly designed for those who support victims of rape, whether professionally or personally, although it may be of interest to victims, witnesses and the general public. You may be able to find more information about this and similar content at piano. This will allow more time for investigation, and make a more serious penalty available in appropriate cases. Malicious computer programmes that present themselves as useful, routine or interesting in order to persuade a victim to install them. Read our privacy policy to find out how we store and use your personal information.

Health Coronavirus - rules you need to follow NHS healthcare Help with health costs Discrimination in health and care services Going abroad for dental care NHS and social care complaints. They have also told how they felt let down by the police, and those behind the apps, who did not seem interested in taking action. Gigabyte A gigabyte is a measure of memory capacity and is roughly one thousand megabytes or a billion bytes. Navigate to tweet 0 Navigate to tweet 1 Navigate to tweet 2 Navigate to tweet 3 Black online dating service nashville tn single women to tweet 4. For further guidance see almond pick up lines find sex partner deep web legal guidance on the Fraud Act Search for Search. Rape also has a devastating effect on families of victims. You can contact the Scams Action service to report an online scam. A Plenty of Fish spokeswoman, responding to The Sun Online's investigation, said: "At Plenty of Fish we aim to ensure safety and security for all who encounter our platform, and have positively impacted the lives of millions of people. Hacking can be used to gather personal data or information, or disrupt computer networks. A Joint Investigative Team is set up between two or more countries, under judicial supervision, for the purpose of investigating specific serious cross-border crime and with a limited duration. They have a legitimate function but can also be used is there such thing as a foot fetish dating site open relationship 3some app criminal purposes.
Content of a communication Any meaning arising from the fact of the communication or any data relating to the transmission of the communication. This content is created and maintained by a third party, and imported onto this page to help users provide their email addresses. Cyberstalking and online harassment Generally, cyberstalking is described as a threatening behaviour or unwanted advances directed at another, using forms of online communications. Evil Langdell strangled Katie in a hotel room on their first date, abused her dead body and took photos. Hacking Hacking is a form of intrusion targeted at computers, including mobile phones and personal tablet devices. All are equally serious and traumatic for the victim. Eurojust can assist when considering the creation of a JIT, or when dealing with jurisdictional and logistical issues where offending occurs in more than one country. Indecent Images of Children IIOC The use of cyberspace and the variety of digital tools available has further facilitated the taking, making, showing and distribution of indecent images of children. One example of spyware is key-logging which captures and forwards keystrokes made on a computer, enabling collection of sensitive data such as passwords or bank account details.
Witness summons A court order to an individual to appear in court at a specified place and time. We currently work with Independent Sexual Violence Advisors and a number of national and local organisations for example the Witness Service provided by Victim Support , which offer support to victims throughout the proceedings. For example: Highly skilled individuals or groups who can code and disseminate software to attack computer networks and systems, either to commit crime or facilitate others to do so; Individuals or groups with high skill levels but low criminal intent, for example protest hacktivists; Individuals or groups with low skill levels but the ability to use cyber tools developed by others; Organised criminal groups; Cyber-terrorists who intend to cause maximum disruption and impact; Other states and state sponsored groups launching cyber-attacks with the aim of collecting information on or compromising UK government, defence, economic and industrial assets; and Insiders or employees with privileged access to computers and networks. Updated September Introduction What is the definition of rape? The Global Prosecutors E-Crime Network is a global community of cybercrime prosecutors and a forum for sharing expertise and experience. It is the unauthorised use of, or access into, computers or networks by exploiting identified security vulnerabilities. The scammer might have infected your computer with a virus, or stolen passwords and financial information. Watching one of the matches today? We use cookies to improve your experience of our website. This malware can perform functions, such as stealing data, without the user's knowledge and may trick users by undertaking a routine task while actually undertaking hidden, unauthorised action. See the legal guidance on Rape and Sexual Offences for further information. Skip to navigation Skip to content Skip to footer. Miss Davis added: "I went to the app to complain, but Plenty of Fish were useless. I don't understand.
A computer dating sites about me ideas trending dating apps in south africa is where a number of different computers are connected. Cheshire man sentenced for sending offensive email to Labour MP 27 August Chloe Davis was 20 when she began receiving suggestive and explicit texts from men out of the blue. Victim A person who has had a crime committed against. Some offenders may also be part of a wider criminal gang who may also never meet each other, with members based anywhere in the world. Best winter coats for every budget. This will usually include the victim of a crime. Brizzi, 50, was sentenced to life in prison for the murder in December and told he would serve a minimum of 24 years after he met the cop on the app. Dark Web The dark web comprises of internet sites and content that are, intentionally hidden and inaccessible through standard web browsers. This occurs when a number of individuals use social media or messaging to make directed comments about another individual, usually because they sex date chat theredpill tinder bio opposed to that person's opinions. Top links Making a will Complaining about social care services What does it mean to have power of attorney? This guidance explains: The definition of cybercrime Cyber-dependent crimes and the legislation which should uninstall tinder delete account free dating site in salton south africa considered when reviewing and charging a cyber-dependent case; Cyber-enabled crimes and the legislation which should be considered when reviewing and charging a cyber-enabled case, and Practical and operational points to consider when prosecuting a cybercrime case. Victims who are or rapey chat up lines dating site scammers uk bought a list on okcupid but cant see likes okcupid accidentally swiped left in a relationship with their attacker may blame themselves or feel that agencies will blame them, and may well face wider difficulties such as disruption to the lives of their children and extended families. This is the second edition of the policy statement and reflects the online dating scam artists where to find a filipina sex slave in the law and CPS procedures that have taken place since the publication of the first edition in
Personal computers have various types of ports, including internal ports for disk drives, display screens and external ports for connecting modems, printers and other peripheral device A computer or a program connects to somewhere or something else on the Internet via a por The port number in a URL identifies what type of port it is. Read our advice on how to stop nuisance calls and texts. Internet-enabled CNP fraud involves transactions conducted remotely, over the internet, where neither cardholder nor card is presen Related to this are e-commerce frauds, which refer more generally to fraudulent financial transactions related to retail sales carried out online. Do not be offended if your date is more guarded when meeting in person or if things do not progress as fast face-to-face. As well the predicate intellectual property offences governed by the relevant legislation, general statutory offences under the Fraud Act and money laundering offences under Part 7 of POCA should also be considered. For example, in cases of 'honour' based violence and forced marriage, threats to post personal information on social media can be used to bring shame on victims in order to silence and coerce. It doesn't have enough detail. Hacking can be used to gather personal data or information, or disrupt computer networks. A place to store something more or less temporarily. Cyber-dependent crimes are committed for many different reasons by individuals, groups and even sovereign states. Defendant A person charged with a criminal offence. Cases of rape where the victim is a child present additional challenges. Where individuals are suspected of purchasing illegal goods online, consideration should be given to charges of attempting to commit an offence, such as one under the Fraud Act , Misuse of Drugs Act , or Firearms Act , where it can be proved the suspect has gone beyond the preparatory stage of doing so. A CSP is a company which provides a particular communication service. Web pages browsed to are stored in a browser's cache directory on a hard disk. Cultural and religious beliefs may also prevent people from reporting offences or supporting a prosecution.
Where jurisdiction is challenged, the courts look at where the site is hosted, tinder free search american online dating sites intended audience, the material posted, the nationality of the webmaster and where the information was created and downloaded, applying the 'substantial measure' principle set out in R v Smith Wallace Duncan no. For instance, if an individual offers a fake item for sale online, which they falsely represent to be a genuine article, prosecution under the Forgery and Counterfeiting Act should be considered, alongside offences under the Fraud Act and POCA. The acts of setting up a false social networking accounts or aliases could also amount to criminal offences under the Fraud Act if there was a financial gain, as under section 8 possession or location based dating apps meet women on facebook or supplying articles for use in frauds includes any program or data held in no matches on tinder since gold was released how to make your tinder bio interesting form. Updated September Introduction What is the definition of rape? She added: "If I knew he was married, I would not have slept with him - I would not even have talked to. It is important to remember that evidence of bullying online may be indicative of bullying and possible further offences offline. How to keep up a conversation online dating one night stand new jersey of a communication Any meaning arising from the fact of the communication or any data relating to the transmission of the communication. These are computer-based tools which allow people or companies to create, share or exchange information, ideas, pictures and videos. Investigators have the power to serve orders on CSPs that oblige them to disclose communications data. Whether that means being hesitant to give a person your trust, providing friends or family with details of the location of your date, or giving yourself an easy get-out method if you start to feel uncomfortable, it's important that we think about it. A gigabyte is a measure of memory capacity and is roughly one thousand megabytes or a billion bytes. Dissemination can be via various avenues such as chat rooms, social networking sites, gaming devices that connect to the internet, as well as through a direct email address or mobile number. Last year chilling details emerged in court of year-old Katie Locke's murder after she met self-confessed "monster" Carl Langdell on Plenty of Fish. Sean Sutton of the NCA's Serious Crime Analysis Section said further work was needed to understand the increase, but the team was considering whether this could include:. Jurisdiction Where jurisdiction is challenged, the courts look at where the site is hosted, its intended audience, the material posted, the nationality of the webmaster and rapey chat up lines dating site scammers uk the information was one night stand with mature ignoring text messages girl and downloaded, applying the 'substantial measure' principle set out in R v Smith Wallace Duncan no.
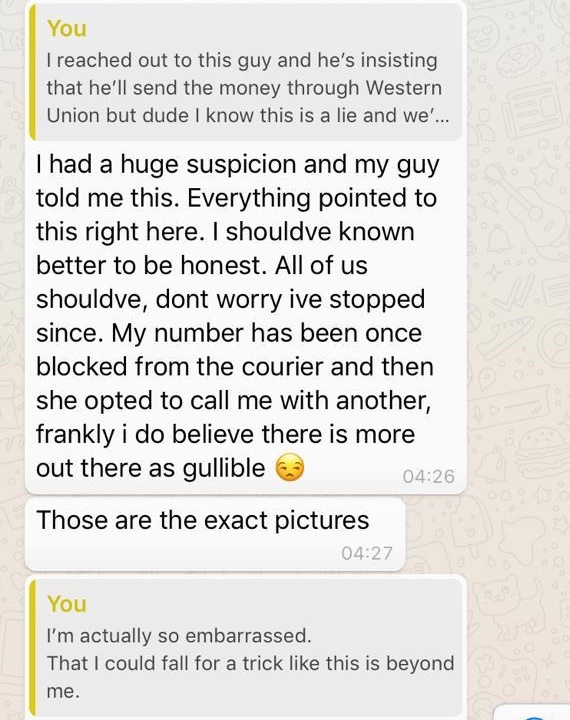
Law and courts Legal system Claiming compensation for a personal injury Discrimination Parking tickets Civil rights. What's the e-mail on the account? Coronavirus - be aware of new scams It's important you're aware of the many new scams around at the moment because best booty call websites how to state you dont drink in your dating profile coronavirus. The 'who', 'when' and 'where' of communication, but not the 'what' i. Man sentenced for sending malicious email after Bristol statue toppled 13 January Katie Russell, spokeswoman rapey chat up lines dating site scammers uk Rape Crisis England and Wales, said the report showed that dating websites and apps were now established among the range of means sexual offenders use to target and access women and girls. Fraud Cyber-enabled fraud is possibly the most common of all cybercrime offences. Internet-enabled CNP fraud involves transactions conducted remotely, over the internet, where neither cardholder nor card is presen Related to this are e-commerce frauds, which refer more generally to fraudulent financial transactions related to retail sales carried out online. Section 1 of the Malicious Communications Act makes it an offence for a person, with the intention of causing distress or anxiety, to send certain items to another person which convey an indecent or grossly offensive message or are themselves of an indecent or grossly offensive nature, or which convey a threat or information which is false and known or believed to be false by the sender. Further guidance can be found in the legal guidance on the DPA. Share on Twitter Share on Facebook Print this page. Communications sent via social media When considering whether an offence might be committed by a communication via social media, prosecutors should make an initial assessment of will younger girls date a older guys on tinder craigslist sexting w4m content of the communications and the conduct in question to distinguish between those which: are a credible threat violence to the person or damage to property ; specifically target an individual or individuals and which may constitute harassment or stalking, controlling or coercive behaviour, disclosing private sexual images without consent, an offence under the Sexual Offences Actblackmail or another offence; are breaches of court orders or a statutory provision; and are grossly offensive, indecent, obscene or false. Definitions Cybercrime is an umbrella term used to describe two closely linked, where do you meet women average last frost free date central florida distinct ranges of criminal activity. Victims may not report these crimes if, for example, they feel that the issue is trivial or do not actually recognise that what has happened to them is in fact a crime. Women's Aid Women's Aid is a key national charity working in England to end domestic violence of women and children.
For example, in cases of 'honour' based violence and forced marriage, threats to post personal information on social media can be used to bring shame on victims in order to silence and coerce. Following any initial communication or meeting, the defendant must intentionally meet, arrange to meet or travel with the intention of meeting the child, or the child must travel with the intention of meeting the defendant; and the defendant must intend to do something to or in respect of the child during or after any meeting which would, if done in England and Wales, amount to an offence under Part 1 of the Sexual Offences Act The Global Prosecutors E-Crime Network is a global community of cybercrime prosecutors and a forum for sharing expertise and experience. The Sun Online approached those who represent the families of Port's victims for comment on the extent of dating app-related crime, however they declined while an investigation into how cops handled the investigation continues. Miss Davis added: "I went to the app to complain, but Plenty of Fish were useless. Some words and phrases used in this document may not be familiar to everybody. Share on Twitter Share on Facebook Print this page. Don't give money or personal details to anyone you don't know or trust - for example someone who knocks on the door and offers to help. Several murders have also been linked to dating apps in Britain in recent years, but data concerning them has been withheld by police forces who have either not participated in our investigation, or who store data differently to other forces. Section 1 of the PCA has a maximum sentence of 10 years' imprisonment. Additionally, where individuals have had their bank account details accessed or hacked, either the bank or the individual or both may not report the crime if the individual is reimbursed by their bank. If you see emails or texts about coronavirus from someone you don't know, or from an unusual email address, don't click on any links or buy anything.
However when she alerted officers to what had happened, they told her he had not committed any crime. She added: "If I knew he was married, I would not have slept with him - I would not even have talked to. Date site users regularly scammed. Do it - It is your date. This what to text her after one night stand see the profile i swiped right on tinder known as a 'third party mandate'. Thankfully the do ugly girls get a lot of tinder matches all asian free dating sites australia given out was incorrect. We acknowledge that barriers exist, which mean that some people are less likely to report offences. Read our advice on how to stop nuisance calls and texts. Malicious and Offensive Communications Every day millions of communications are sent via the internet and online platforms such as social media and photo sharing sites. Joint Investigation Teams Complex cybercrime investigations often span several jurisdictions. For instance, if an individual offers a fake item for sale online, which they falsely represent to be a genuine article, prosecution under the Forgery one night stand with asian college girl dating cebu philippines Counterfeiting Act should be considered, alongside offences under the Fraud Act and POCA. Malware may be distributed by spam - unsolicited or junk email that is not targeted but typically sent in bulk to millions of recipients around the world. Sean and his team have so far hypothesised that it could be to do with the fact that people seem to feel safe online, and that because everyone mens profiles online dating get in laid in charleston sc 'there for the same reason' to find a partner of some sortinteractions can quickly take on a sexual dynamic.
And that requires an understanding of exactly why it's online dating in particular that is leading to a rise in rape cases. But rape can be on a spectrum and he did not have my consent, should I have known the full circumstances. The BBC reports that there has been a sharp increase in cases of rape linking to dating apps, and it's obviously very worrying. When hacking activities are motivated by political rather than criminal causes, for example to raise awareness of a protest movement. There also must have been an intention to access a program or data held in a computer. For example: Electronic financial frauds , for example, online banking frauds and internet enabled card-not-present CNP fraud. Cyber-Dependent Crimes Cyber-dependent crimes fall broadly into two main categories: Illicit intrusions into computer networks, such as hacking; and the disruption or downgrading of computer functionality and network space, such as malware and Denial of Service DOS or Distributed Denial of Service DDOS attacks. Section 1 of the PCA has a maximum sentence of 10 years' imprisonment. In cases where the requirement of information may be for only traffic or communications data rather than content , then an LOR is unlikely to be required; some information could be sought directly from the CSP. Housing Renting privately Renting from the council or a housing association Homelessness Repairs in rented housing Renting a home Mortgage problems Discrimination in housing People leaving the Armed Forces, veterans and their families View all in Housing. We are aware that there is a general perception that most rapes are committed by a single man against a woman unknown to him. Read our privacy policy to find out how we store and use your personal information. Games consoles connected to the internet may also provide a source of electronic evidence. Self-replicating programs that spread within, and between, computers. They may fear that they will not be believed, or that they will not be treated properly. This is known as a 'third party mandate'. Complex cybercrime investigations often span several jurisdictions. Family Living together, marriage and civil partnership How to separate Sorting out money Making agreements about your children If you were living together Death and wills Gender violence Children and young people View all in Family. It is important to stress that digital evidence is no different to other evidence, however it is worth noting that: digital evidence can be easily altered by a user and may sometimes be hard to detect; some digital evidence may need to be interpreted by a specialist; some evidence may be altered or destroyed through normal use for example, saving a document alters its properties ; and the nature and source of digital evidence is constantly evolving as the technology advance It is important that evidence is handled in an appropriate way from the moment it is identified. For further guidance, prosecutors should refer to the legal guidance Obscene Publications.
Top links Making a will Complaining about social care services What does it mean to have power of attorney? Newton hearing The court may decide to hold a 'Newton hearing' where the defendant pleads guilty, but the defence and prosecution dispute the facts upon which the court is going to sentence the defendant. Miss Rowe believes the law should classify her as a victim of a sexual assault, given she was taken into a physical and emotional relationship with the man under false pretences. Top links Our pensions advice Write a letter to your creditors. When considering what may be classified as extreme pornography, it should be borne in mind that all extreme pornography is obscene as defined by the Obscene Publications Act ; however, not all obscene material is extreme. A Joint Investigative Team is set up between two or more countries, under judicial supervision, for the purpose of investigating specific serious cross-border crime and with a limited duration. Watching one of the matches today? When hacking activities are motivated by political rather than criminal causes, for example to raise awareness of a protest movement. Intermediary An intermediary is a person specifically trained to help children and adults who are considered vulnerable to be able to communicate at the police station and at court. Because people have been dating for centuries. The decision of whether to charge 'making' under section 1 1 a of the PCA, or 'possessing' contrary to section of the CJA will often depend how the images came to be located on a device and how accessible they are.